
The DKIM Record Explained
Do you need to set up a DKIM record on your domain DNS, but you’re not sure what it is and how to do it?
Search no longer! In this post we’ll explain everything you need to know about DKIM records.
What Is a DKIM Record
DKIM stands for DomainKeys Identified Mail. It’s a way of ensuring emails integrity using encryption keys. We’ll explore in depth what that means exactly.
A DKIM record is a type of DNS record. More precisely, it’s a TXT record. If you’re not familiar with DNS records, you’ll get answers in our post DNS Records Explained.
This is what a raw DKIM record looks like:
s20220226168._domainkey.myawesomedomain.com. 3600 IN TXT "k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAukTJzbjp14QWQKKuI10JQatEkzI+XFDsqBU+Rs8QbIeTlHTeN8sVsGlxfWl2gEMOjO7RRHNmfcQrC6Xi11HAbB6J/fcTAJHSZk0xvKAdtGw4XE+B0ok6rZHAhNWmEYZAUb+2s0kfVYA+c2kzefAcDe0v0MghNTNfNkh8vSz30c5FpsVShuuFyfv4DMFkaIUo+kMQw" "4CfEHEhaz+o706GCV4wz8RNDXWXm9KZSTdIY/uYpAriSk8qUF3lmEqLBTCPtfDH30wGD/wuWBLJFYrtHfxyHLoJvm7sxkGuVERLNVf3QLQ/IAFK6uTaTkMJJqCNf3eNoECt+WJ6X8oP7C+xJQIDAQAB"In all TXT records the first part is the host, or name. Usually that’s just the root domain name (myawesomedomain.com in this case). As you can see however, here the root domain name is prefixed with s20220226168._domainkey.
The _domainkey part indicates this is a DKIM record. The s20220226168 part is what’s called a “selector”.
The selector is an arbitrary string used to identify a particular DKIM record, in case a domain would have multiple ones. Often, it contains the date and time the DKIM key was created, but it can be anything.
What’s the DKIM key? Glad you asked! That’s the long part inside double quotes. It’s called a key because that’s what it is, a public encryption key.
DKIM records are public encryption keys. They are provided by your mail service and are used by recipient mail servers to verify the digital signature of emails (i.e. their integrity).
In other words, DKIM records allow recipient mail servers to verify emails haven’t been tampered with after they were sent from the sender mail server.
An email passing the DKIM test will therefore be more trusted, while an email failing the test will be more likely to get a bad spam score.
I know, this is all pretty vague at this point, so let’s see how DKIM works exactly.
How DKIM Records Work
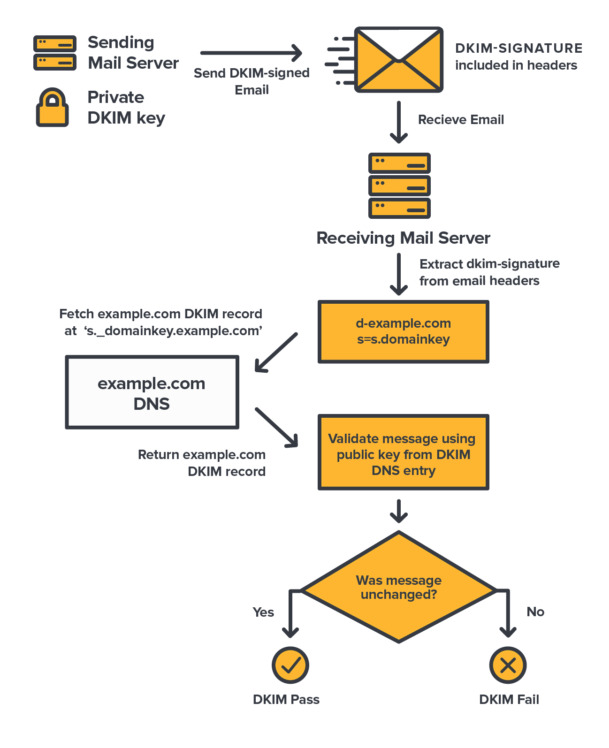
When you send an email from a mail app, the app talks with your sending mail server, which in turns sends your email to your recipient mail server (more on this process here).
But your mail server does something else before it sends the email: it adds a DKIM-Signature header in the email headers (the stuff you see at the top of an email body when you open the email “source”).
A DKIM-Signature header looks like this:
DKIM-Signature: v=1;a=rsa-sha256;bh=J4AMIWuCU9FdjX5lhw84sIWkv8pEHVpjycMbsMY3jmM=;c=relaxed/simple;d=myawesomedomain.com;h=from:subject:date:message-id:to:mime-version;s=s20220226168;b=YvhOsGBmb+37w58rMaCRnEU7GYP3lyMhfdOklyVysgP7QnQRSFkInZaa5rsMgI+LAxfl+ubpVKRv61W9OllZa7qrAZAfzkNL+oug0eVN9nTLuzHbvNWBhEz08PDSTeU3JZO/hb7y4NMIVYd+eiYYubhwdlCHl4KbTQpoZ22TR78=It contains multiple informations like the DKIM version (v= tag), encryption algorithm (a= tag), domain (d= tag), selector (s= tag), and, critically, the email encrypted signature (b= tag).
The signature represents a digital fingerprint of your email, also called a “hash”. Your mail server generates it and encrypts it using the private key associated with your DKIM public key.
About encryption keys
If you’re not familiar with encryption that’s ok. All you need to know is that two keys are required: a private one, and a public one.
The private key is secret and only your mail server knows about it. It can be used to encrypt data. The public key is visible to the entire world (it’s in your DKIM record), and can be used to decrypt data previously encrypted with the private key.
The trick is that only data which has been encrypted with the private key associated with a public key will be correctly decrypted by that public key.
Okay, great, but what’s that used for?
The DKIM header is used by the recipient mail server to decrypt and verify the email signature. To do so, the server:
- Fetches the DKIM record indicated by the domain and selector given in the email DKIM header (
dandstags). - Uses the public key in the DKIM record to decrypt the encrypted signature.
- Computes its own signature of the email.
- Compares both signatures.
If both are not identical, the email has been tampered with, and the DKIM test fails.
What happens after the DKIM test fails depends on the anti-spam policy of the recipient’s mail server. Usually, the email will be considered as spam.
Why Having a DKIM Record Is Important
The DKIM standard was created to fight email forgery and tampering, commonly used in phishing.
When the DKIM test passes, a recipient is assured the email wasn’t altered after it was sent. DKIM better protects your domain against impersonators, though, as we’ll see, that protection is limited when SPF and DMARC are not used alongside DKIM.
This in itself is enough of a reason to use DKIM, but there are at least two other critical reasons which are a consequence of the first.
Due to the integrity guarantee DKIM represents, anti spams systems will grade an email differently depending on whether it passes or fails the DKIM test, or doesn’t use DKIM in the first place.
An email passing the test will be more likely to be seen as legitimate than an email not using DKIM, or worse, failing the test. In the latter case the email will be far more likely to be considered as junk or spam.
In other words, DKIM impacts the deliverability of your emails. If you want to make sure your emails get the best chances to be delivered successfully to you recipients, you must use DKIM.
The last major reason is domain reputation. By using DKIM, you are reducing the amount of email abuses with your domain, and doing so, you’re increasing your domain overall reputation to mail services and other Internet services around the world. Over time, you’re building trust, and your domain emails deliverability will be further enhanced by it. DKIM improves your domain reputation.

What DKIM Records You Should Use
The domain you’re using to send emails should have a DKIM record for each and every mail service sending emails from one of your domain addresses.
The first one is of course your domain email service, responsible for hosting your domain email addresses and sending your regular emails to your recipients.
But that may not be it. If you’re using some sort of CMS or website builder doing email sending on behalf of your domain name (e.g. transactional email), like Shopify or Wix, you’ll want to make sure they provide you with a DKIM record for their mail servers, to add to your domain DNS.
Similarly, if you’re using a third party mail service for marketing campaigns, be sure to have a DKIM record for that service as well.
How to Set Your DKIM Record
As usual DNS records are set at your domain provider website, in the DNS editor section. Here’s a list of DNS guides for common providers.
To know what values you need as selector and public key, you’ll have to look up into your mail service account.
At postale.io for instance you’ll find that in the DKIM section of your domain page in the admin interface. You can just copy/paste the record to your DNS.

How to Check Your DKIM Record
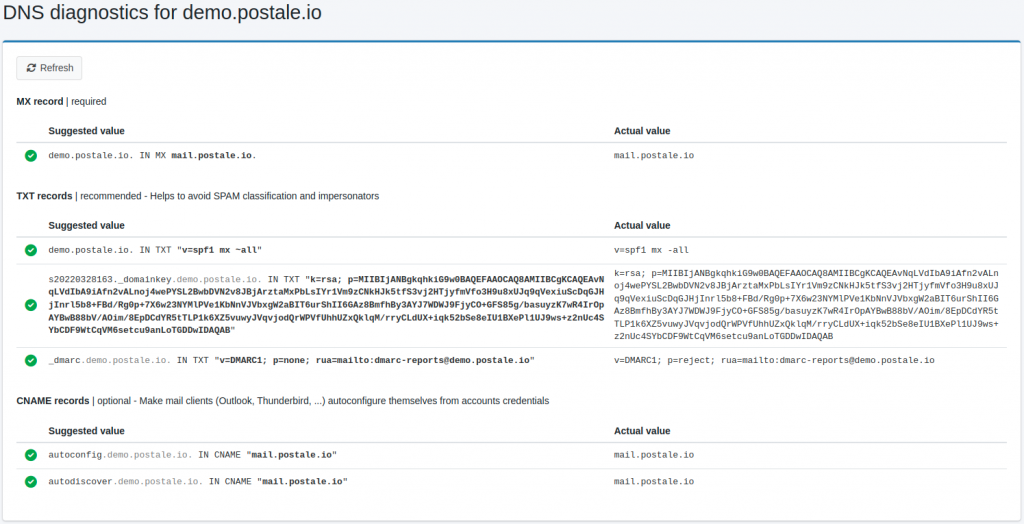
There are many tools out there to look up your DKIM record. If you like the command line, the good old dig command works great.
peter@home:~$ dig TXT s20220226168._domainkey.yourdomain.com.
; <<>> DiG 9.16.1-Ubuntu <<>> TXT s20220226168._domainkey.demo.postale.io.
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29549
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;s20220226168._domainkey.yourdomain.com. IN TXT
;; ANSWER SECTION:
s20220226168._domainkey.yourdomain.com. 3600 IN TXT "k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAukTJzbjp14QWQKKuI10JQatEkzI+XFDsqBU+Rs8QbIeTlHTeN8sVsGlxfWl2gEMOjO7RRHNmfcQrC6Xi11HAbB6J/fcTAJHSZk0xvKAdtGw4XE+B0ok6rZHAhNWmEYZAUb+2s0kfVYA+c2kzefAcDe0v0MghNTNfNkh8vSz30c5FpsVShuuFyfv4DMFkaIUo+kMQw" "4CfEHEhaz+o706GCV4wz8RNDXWXm9KZSTdIY/uYpAriSk8qUF3lmEqLBTCPtfDH30wGD/wuWBLJFYrtHfxyHLoJvm7sxkGuVERLNVf3QLQ/IAFK6uTaTkMJJqCNf3eNoECt+WJ6X8oP7C+xJQIDAQAB"
;; Query time: 44 msec
;; SERVER: 127.0.0.53#53(127.0.0.53)
;; WHEN: mar. avril 26 18:06:16 CEST 2022
;; MSG SIZE rcvd: 483For more intuitive tools, have a look at mxtoolbox.com’s DKIM checker, or the one from mail-tester.com. postale.io also has an all-in-one DNS diagnostic tool, available from your domain page in the admin interface.
Why DKIM Alone Is Not Enough
This is all well and good, but in reality the DKIM record is not enough to protect your emails from tampering and impersonators.
The reason for that lies partly in the From header field. That’s another email header defined by the SMTP protocol, the language in which mail servers speak.
The From header should be set to the email address of the sender, but the protocol actually allows one to put any email address there, even if that’s not the one really sending (i.e. the one the sender is authenticated with on his/her mail server).
The “real” address is also in the email headers (in the Return-Path one, also called envelope sender), but the thing is, the sender email address people see in mail apps is usually taken from the From header.
This means an abuser could impersonate you while still passing the DKIM test. He/she would simply need an arbitrary email address with a valid DKIM record and tell his/her mail server to set the From field to your address.
Or, he/she could send a forged email without DKIM header, skipping the DKIM test altogether, possibly even using your domain address as envelope sender in that case.
In addition, DKIM doesn’t enforce any action by itself. Recipient mail servers are free to apply any policy they deem appropriate whenever an email fails the DKIM test, including delivering it into the recipient inbox.

But do not despair! We haven’t done all that tedious work for nothing, far from it. This is were we call on to the SPF and DMARC records.
Beyond DKIM: The Need for SPF and DMARC Records
If your domain doesn’t have an SPF record, well, you should fix that asap.
An SPF record specifies which mail server IP addresses are allowed to send on behalf of a domain name, and the SPF test conducted by recipient mail servers is based on the SPF record of the domain in the Return-Path address (a.k.a envelope sender).
With an SPF record, you’re making it harder for an abuser to spoof the envelope sender address even if he/she skips the DKIM test, because you allow only legitimate mail servers to use your domain address as envelope sender.
And the definitive protection factor will be the DMARC record. That one will ensure the email address in the From header field matches the envelope address. It also enables you to enforce a policy whenever SPF or DKIM tests fail, and monitor abuse attempts.
Used alongside DKIM and SPF, DMARC provides a strong protection, and great deliverability. Don’t miss out on it!
Related Posts
-

The SPF Record Explained
If you’re here you’ve probably been asked to configure your domain SPF record while setting up a business email address. If you’re not sure what that is, you’re in the right place! In this post we’ll explain what the SPF record is, and how to set it up correctly. What Is an SPF Record SPF…
-

The DMARC Record Explained
In this post we’ll explore in detail what a DMARC record is, why you should absolutely have one, and how to use it. If you want to understand DMARC, come along! What Is a DMARC Record DMARC stands for Domain-based Message Authentication, Reporting and Conformance. Quite a mouthful. It designates a system allowing domain owners…